The focus of the collaboration industry over the last few weeks has been around security.
The firestorm started when security researcher Jonathan Leitschuh published a
detailed write-up covering vulnerabilities he had discovered in the Zoom video conferencing service that allowed for potential denial-of-service attacks, unwanted joining of meetings (potentially with microphone and camera activated), and perhaps most disturbingly, a resident Web server that was left behind on uninstall, enabling the re-installation of the Zoom client, and the joining of a person to a Zoom meeting, without a user’s consent.
No Jitter’s Beth Schultz covered the story, and Zoom’s response
here while contributor and fellow analyst Dave Michels, of TalkingPointz, provided a thoughtful look back at Zoom’s response and the continued questions raised by the incident
here.
The security stories continued last week with Slack’s
announcement that it was resetting all user passwords for accounts it believes were compromised in a 2015 data breach, and a new
post by Cisco Distinguished Security Engineer Jeremy Laurenson on how allowing guest accounts with Microsoft Teams means organizations lose control of data shared into someone else’s Teams instance. Jeremy’s post echoes concerns related to guest accounts that I touched on in a
No Jitter post back in May 2018.
Sadly, the recent security-related stories underscore the lack of risk awareness, and inclusion of collaboration in overall security strategies. In our recently published "
Workplace Collaboration: 2019-20 Research Study," Nemertes found that just 21.3% of the 645 participating organizations have a proactive workplace collaboration security strategy. That’s up slightly from 2018 when just 19.3% of participants said they had such a strategy.
Today, most enterprise security strategies are evolving from perimeter-based approaches to
zero-trust models that treat all devices and users as untrusted. Too often, however, enterprise focus those efforts on protecting access to data stored in CRM, ERP, and other apps, and not necessarily covering collaboration platforms and services.
We found that having a proactive workplace collaboration security strategy correlates with success (defined as obtaining measurable business value from collaboration investments). Approximately 17% of our research participants qualified for our success group. Of those, 36% have a proactive security strategy covering collaboration versus just 21.1% of those not in our success group.
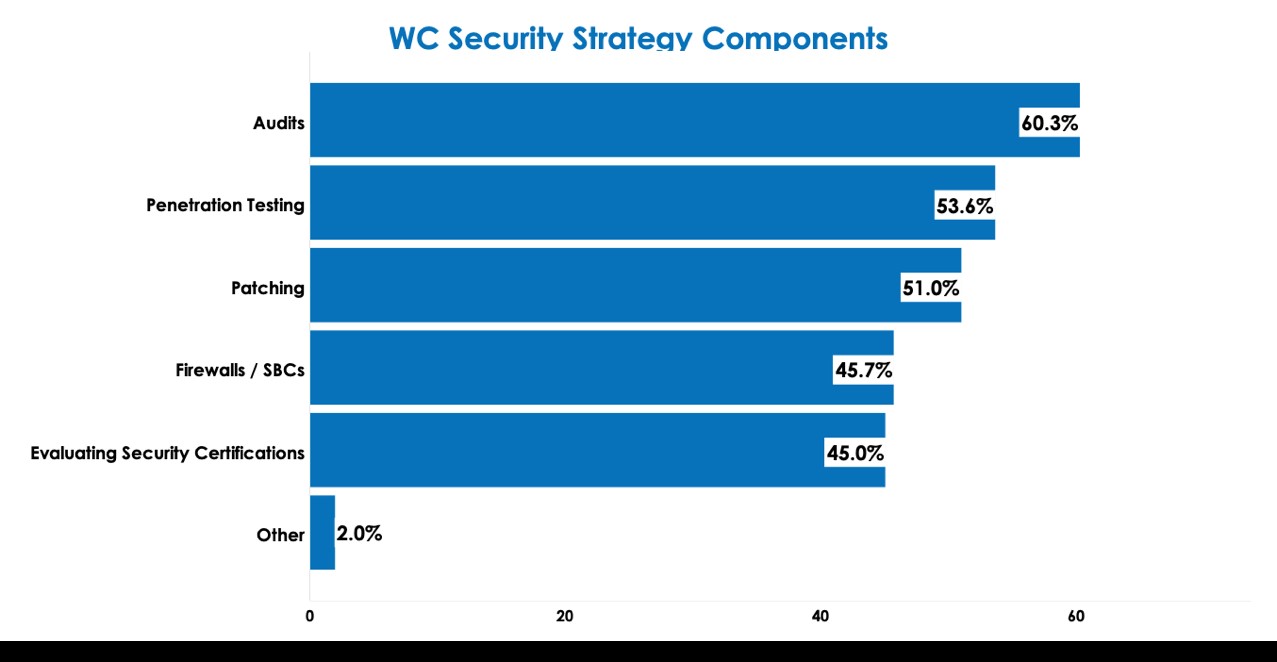
We dug a bit deeper to better understand what participants who had a proactive security strategy were including in that effort. The primary components are:
- Regular audits, by internal security teams or external vendors, to discover potential vulnerabilities
- Penetration testing, again by internal teams or via external vendors, to discover potential paths to access applications by unauthorized individuals
- Patching programs to identify, evaluate, and apply security patches as they become available
- Implementing of firewalls and/or session border controllers to provide protection against SIP-based application attacks
- Ensuring that vendors obtain relevant compliance and security certifications such as FedRAMP, SOC 2/3, ISO/IEC 2700xx, HIPAA, etc.
Most used are security audits, while app-specific firewalls and security certification assessments are least used. We’re not yet finding that organizations are extending zero-trust components like behavioral threat analytics, cloud access security brokers, and next-generation endpoint security to their collaboration applications.
In addition, we’re finding that organizations are increasingly mandating the use of encryption, the ability to manage their own encryption keys, and requiring applications to support single sign-on before allowing lines of business to use their own collaboration applications.
While we didn’t specifically ask about guest account use, anecdotally we do hear that these are typically allowed, likely with little understanding of the risk as Cisco’s Laurenson noted in the post I previously cited. However, organizations wishing to support team collaboration across corporate boundaries should look at using either federation services like Mio, NextPlane, and Sameroom, or enabling native federation provided by Team apps like Cisco Webex Teams.
Hopefully the collaboration security issues of the last few weeks will serve as a wakeup call to both CISOs and collaboration leaders to take security more seriously, and to include collaboration platforms in their overall security planning, especially their emerging zero-trust approaches.