How Crooks Use The Credit Card Data They Steal From eCommerce Websites
- Thousands of credit cards are compromised daily, but what happens with the stolen information?
- Crooks are either creating clone cards and buy expensive items or indulge in online transactions.
- For the first method to work, the scammers will also need to create a counterfeit ID card.
As we saw recently, eCommerce websites are being targeted in bulk by malicious scripts that manage to steal the credit card information of victims. Very often, the operators of the infected platforms don’t realize the problem in time, leaving their customers vulnerable to crooks. A recent post by Sucuri researchers explores what happens after the stealing of the credit card data, showing us what the attackers do with it. For those of you who have fallen victims of such attacks, use the following information to protect yourself in the future.
As Sucuri points out, the actors who stole the payment data in the first place are usually those who will monetize it. The reason why this is preferable to selling the information on darknet forums is that nowadays, financial institutions are quick to respond and revoke the stolen credit cards, so there’s not much time to take advantage of the stolen info. Even if the data is offered for sale, it happens on a limited scale, and it won’t change many hands.
image source: blog.sucuri.net
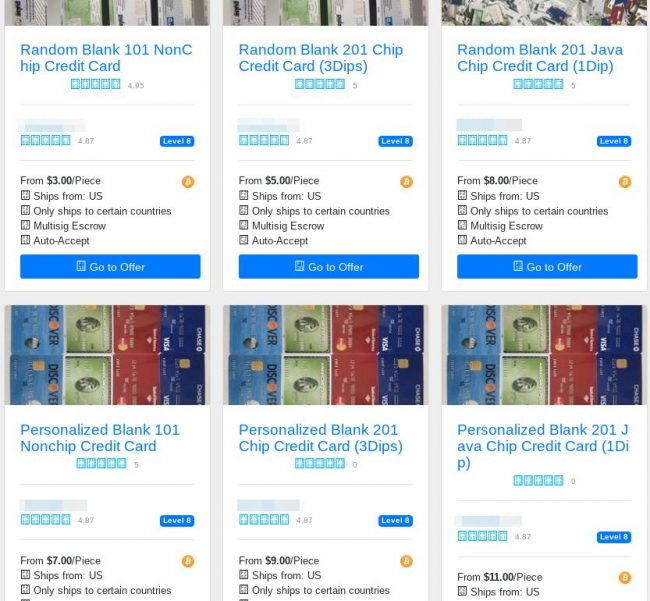
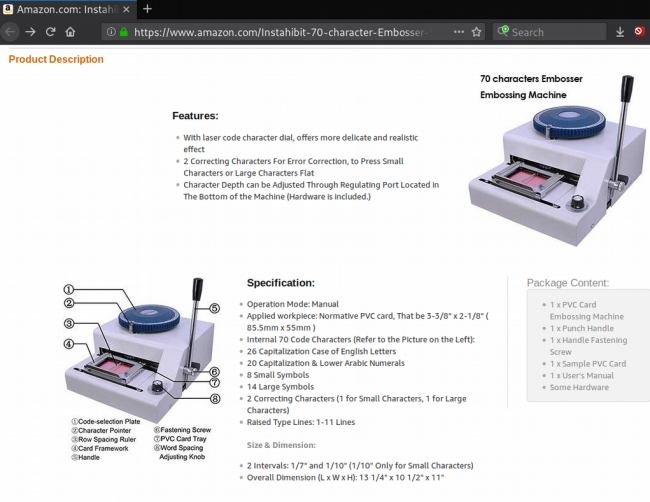
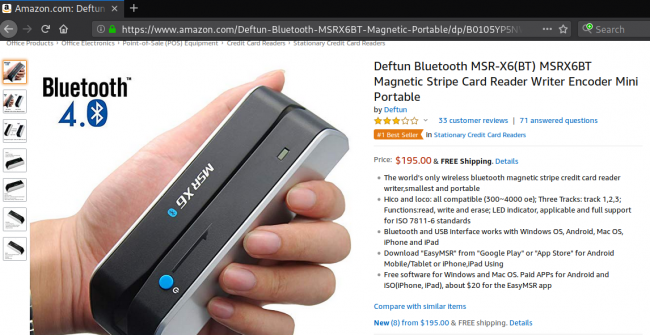
From then on, the most common way of monetizing is through a physical transaction, which is the safest for the crook since it’s anonymous. To do that, they buy “blank payment cards” and load the magnetic stripe with the stolen data using an encoder. Another piece of equipment that is needed for this job is an embosser that will add the name of the owner and the number onto the clone card. These cards are used until the bank account is emptied or the card is revoked. Usually, crooks buy high-value items for reselling purposes. In many cases, the scammers are also creating a counterfeit ID or driver’s license just in case the merchant asks to see it.
image source: blog.sucuri.net
image source: blog.sucuri.net
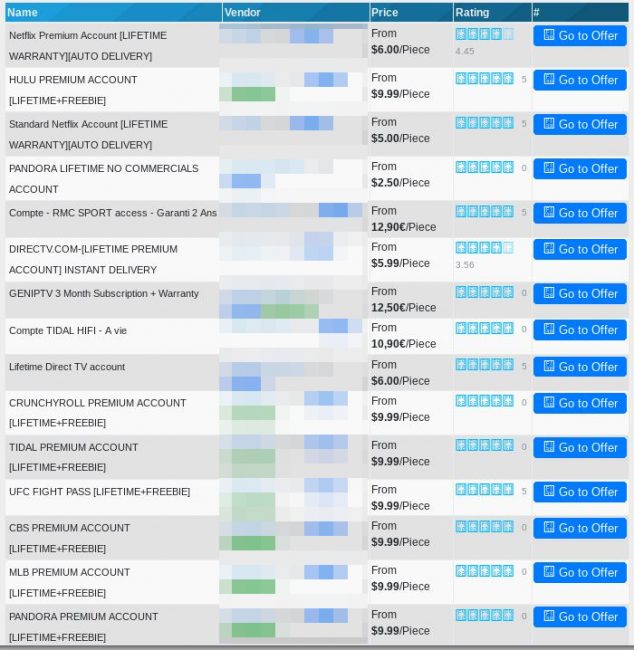
The other way to presume upon the stolen data is through CNP (card not present) transactions where only the stolen data is entered on online platforms. As this is risky, crooks use money mules who accept the money on their bank accounts and then send it to the scammers via Western Union, or other means. Opening a new bank account using fraudulent IDs is both harder and riskier, as “fresh” bank accounts are more rigorously monitored by financial institutions, whereas money mules are using “aged” accounts. Another way of CNP exploitation is for the criminals to buy subscription packages on popular services and then sell them to others at a large discount.
image source: blog.sucuri.net
Have you ever had your credit card information stolen by crooks? Share the details with our community in the comments down below, or on our socials, on Facebook and Twitter.